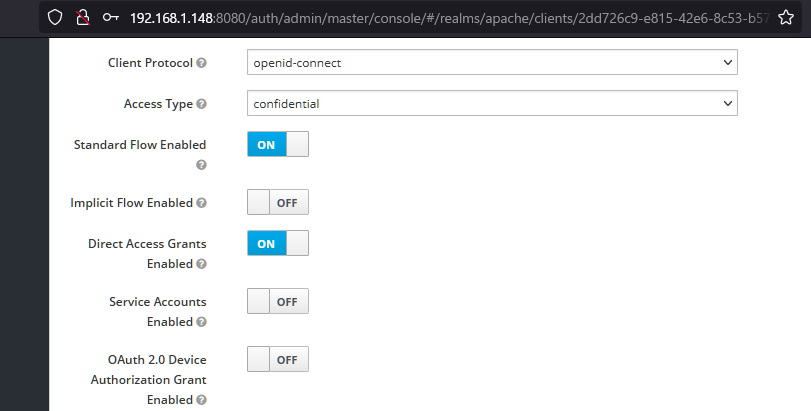
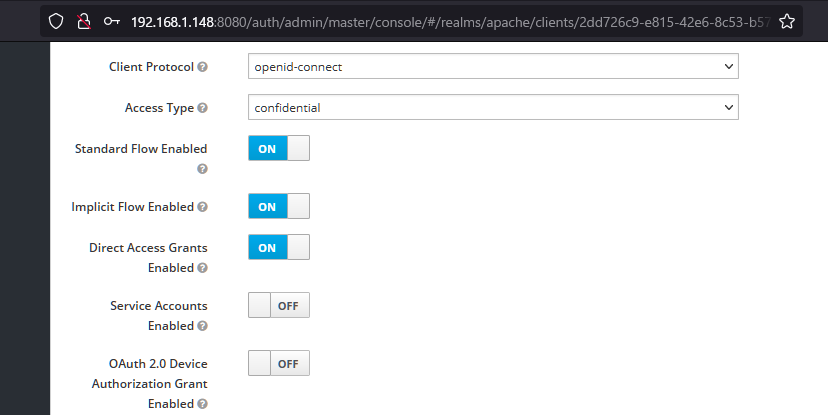
OpenIDにはいくつかのフローがありますが、ここではまず前回試した認可コードフローとインプリシットフローについての差異を詳しく調べてみました。
(リダイレクトによる連携などをするフローはこの二つ)
※クライアント・クレデンシャルズフローについて、またPKCEについて最下部に追記(2023/4/7)
「OAuth 2.0 全フローの図解と動画」
https://qiita.com/TakahikoKawasaki/items/200951e5b5929f840a1f
「KeycloakでOpenID Connectを使ってシングルサインオンをしてみる(認可コードフロー(Authorization Code Flow)編)」
https://qiita.com/rawr/items/d4f45e094c39ef43cbdf
「KeycloakでOpenID Connectを使ってシングルサインオンをしてみる(他のフロー(Implicit Flow、Resource Owner Password Credentials、Client Credentials)編」
https://qiita.com/rawr/items/5fde71da850c1f65373a
環境
環境は前回のものと同じですが、KeycloakとApacheのサーバを分けてみました。
Webブラウザ: 192.168.1.228 / Chrome / windows
Keycloak(n07): 192.168.1.148 / Ubuntu 20.04
Apache(n03): 192.168.1.147 / Ubuntu 22.04
また時刻のズレがあると以下のエラーが以下のエラーがでるため、
ブラウザ
OpenID Connect Provider error: Error in handling response type.
/var/log/apache/error.log
[auth_openidc:error] [pid 199611:tid 140239976773184] [client 192.168.1.228:49840] oidc_proto_parse_idtoken: id_token payload could not be validated, aborting, referer: http://192.168.1.147/private/callback
下記のように時間同期サービスの再起動と確認をしました。
sudo systemctl restart systemd-timesyncd.service
timedatectl
auth_openidc.conf
|
1 2 3 4 5 6 7 8 9 10 11 12 |
OIDCProviderMetadataURL http://192.168.1.148:8080/auth/realms/apache/.well-known/openid-configuration OIDCClientID apache24 OIDCClientSecret fdcbdee7-0f0a-4734-890b-0242c803cd3d OIDCResponseType code #OIDCResponseType "token id_token" OIDCScope "openid" OIDCSSLValidateServer Off OIDCProviderTokenEndpointAuth client_secret_basic OIDCRedirectURI http://192.168.1.147/private/callback OIDCCryptoPassphrase passphrase OIDCPreservePost On |
auth_openidc.confは、OIDCResponseTypeを”token id_token”に変更
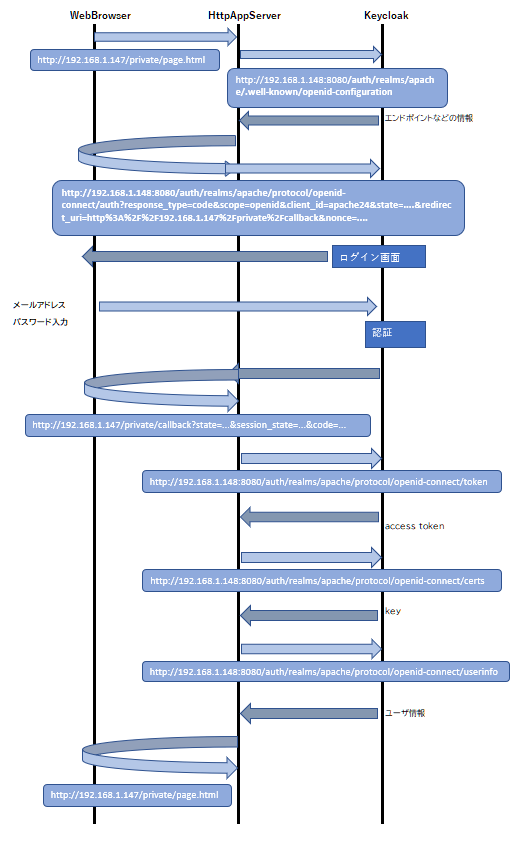
tcpdumpを使って実際に動かしたときのパケットキャプチャをとり(Apache側)、シーケンス図にまとめてみました。(※ログイン時メールアドレスではなく、ユーザ名を入力)
Code Flow
Implicit Flow
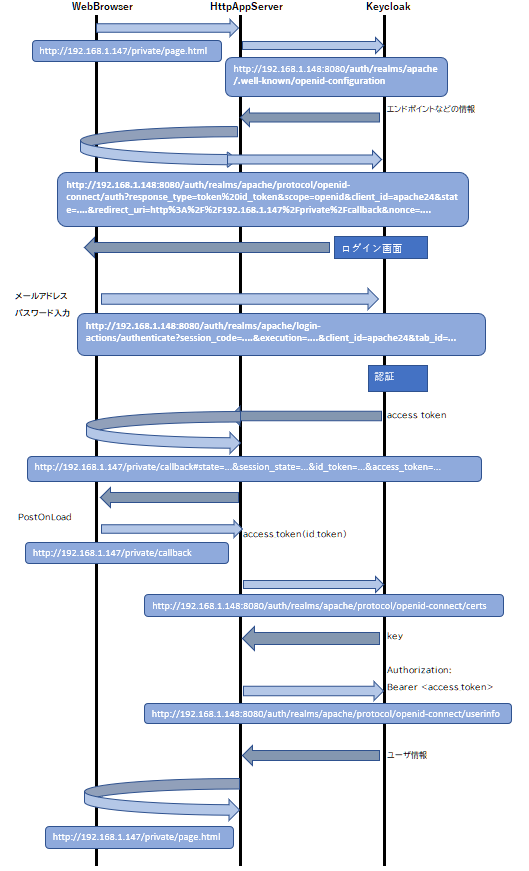
認可コードフローと、インプリシットフローの大きな違いはアクセストークンの受け取り方ですが、その違いを確認することできました。先入観としてインプリシットフローの方がシンプルなのかと思いましたが、そうではありませんでした。
インプリシットフローのアクセストークンを受け取るしくみが、確認ができなかったためKeycloak側のバケットも確認したところ、リダイレクトURLに#が含まれており、パラメータがApache側のtcpdumpに現れないことに気づきました。
またリダイレクトもJavaScriptでPostOnLoadというロード時に、#以下の文字列をバースして変数をセットしてPOSTリダイレクトするという、ちょっとトリッキーなことをやっています。(普通にリダイレクトするとGETになってしまう)
概念図とあわせて実際にパケットを追ってみると理解が深まります。他のフローもまた確認してみたいと思っています。
最後に、長くなりますがパケットキャプチャの結果を載せておきます。(意外と後からいろいろと確認したいことが多いため)
表示制限をしているためLocationヘッダが切れている部分もありますが(トークンがながすぎるため)、実際テストでは、表示数を増やして確認し、上記シーケンス図に反映させています。
CodeFlow
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 |
n@n03:~$ sudo tcpdump -A -s 2048 -i enp0s3 \(\(src host 192.168.1.147\) and \(dst host 192.168.1.228\)\) or \(\(src host 192.168.1.228\) and \(dst host 19 2.168.1.147\)\) or \(\(src host 192.168.1.147\) and \(dst host 192.168.1.148\)\) or \(\(src host 192.168.1.148\) and \(dst host 192.168.1.147\)\) and not port 22 and tcp tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on enp0s3, link-type EN10MB (Ethernet), snapshot length 2048 bytes 07:40:31.877280 IP 192.168.1.228.61961 > n03.http: Flags [S], seq 3415375025, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 E..4-.@...HN......... .P..|......................... 07:40:31.877684 IP n03.http > 192.168.1.228.61961: Flags [S.], seq 216850895, ack 3415375026, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 E..4..@.@............P. ......|..................... 07:40:31.878412 IP 192.168.1.228.61962 > n03.http: Flags [S], seq 1404803842, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 E..4-.@...HM......... .PS............?.............. 07:40:31.878412 IP 192.168.1.228.61961 > n03.http: Flags [.], ack 1, win 513, length 0 E..(-.@...HX......... .P..|.....P............. 07:40:31.878412 IP 192.168.1.228.61961 > n03.http: Flags [P.], seq 1:455, ack 1, win 513, length 454: HTTP: GET /private/page.html HTTP/1.1 E...-.@...F.......... .P..|.....P...t...GET /private/page.html HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 07:40:31.878432 IP n03.http > 192.168.1.228.61962: Flags [S.], seq 3152677841, ack 1404803843, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 E..4..@.@............P. ....S....................... 07:40:31.878558 IP n03.http > 192.168.1.228.61961: Flags [.], ack 455, win 501, length 0 E..(..@.@............P. ......~xP....... 07:40:31.879045 IP 192.168.1.228.61962 > n03.http: Flags [.], ack 1, win 513, length 0 E..(-.@...HV......... .PS.......P....5........ 07:40:31.887748 IP n03.36842 > 192.168.1.148.http-alt: Flags [S], seq 2491717152, win 64240, options [mss 1460,sackOK,TS val 749350288 ecr 0,nop,wscale 7], length 0 E..<.[@.@.................. ................... ,.-......... 07:40:31.888512 IP 192.168.1.148.http-alt > n03.36842: Flags [S.], seq 2724563381, ack 2491717153, win 65160, options [mss 1460,sackOK,TS val 3542351511 ecr 749350288,nop,wscale 7], length 0 E..<..@.@..D.............e.....!............... .#..,.-..... 07:40:31.888569 IP n03.36842 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749350289 ecr 3542351511], length 0 E..4.\@.@..................!.e............. ,.-..#.. 07:40:31.888709 IP n03.36842 > 192.168.1.148.http-alt: Flags [P.], seq 1:139, ack 1, win 502, options [nop,nop,TS val 749350289 ecr 3542351511], length 138: HTTP: GET /auth/realms/apache/.well-known/openid-configuration HTTP/1.1 E....]@.@..e...............!.e.......(..... ,.-..#..GET /auth/realms/apache/.well-known/openid-configuration HTTP/1.1 Host: 192.168.1.148:8080 User-Agent: mod_auth_openidc Accept: */* 07:40:31.889260 IP 192.168.1.148.http-alt > n03.36842: Flags [.], ack 139, win 508, options [nop,nop,TS val 3542351512 ecr 749350289], length 0 E..4.4@.@................e................. .#..,.-. 07:40:31.897959 IP 192.168.1.148.http-alt > n03.36842: Flags [P.], seq 1:6078, ack 139, win 508, options [nop,nop,TS val 3542351520 ecr 749350289], length 6077: HTTP: HTTP/1.1 200 OK E....5@.@..Y.............e...........[..... .#..,.-.HTTP/1.1 200 OK Cache-Control: no-cache, must-revalidate, no-transform, no-store X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:40:31 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 5688 {"issuer":"http://192.168.1.148:8080/auth/realms/apache","authorization_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth","token_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/token","introspection_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/token/introspect","userinfo_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/userinfo","end_session_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/logout","jwks_uri":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/certs","check_session_iframe":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/login-status-iframe.html","grant_types_supported":["authorization_code","implicit","refresh_token","password","client_credentials","urn:ietf:params:oauth:grant-type:device_code","urn:openid:params:grant-type:ciba"],"response_types_supported":["code","none","id_token","token","id_token token","code id_token","code token","code id_token token"],"subject_types_supported":["public","pairwise"],"id_token_signing_alg_values_supported":["PS384","ES384","RS384","HS256","HS512","ES256","RS256","HS384","ES512","PS256","PS512","RS512"],"id_token_encryption_alg_values_supported":["RSA-OAEP","RSA-OAEP-256","RSA1_5"],"id_token_encryption_enc_values_supported":["A256GCM","A192GCM","A128GCM","A128CBC-HS256","A192CBC-HS384","A256CBC-HS512"],"userinfo_signing_alg_values_supported":["PS384","ES384","RS384","HS256","HS512","ES256","RS256","HS384","ES512" 07:40:31.898051 IP n03.36842 > 192.168.1.148.http-alt: Flags [.], ack 6078, win 474, options [nop,nop,TS val 749350298 ecr 3542351520], length 0 E..4.^@.@....................e.s........... ,.-..#.. 07:40:31.898229 IP n03.36842 > 192.168.1.148.http-alt: Flags [F.], seq 139, ack 6078, win 501, options [nop,nop,TS val 749350298 ecr 3542351520], length 0 E..4._@.@....................e.s........... ,.-..#.. 07:40:31.900093 IP 192.168.1.148.http-alt > n03.36842: Flags [F.], seq 6078, ack 140, win 508, options [nop,nop,TS val 3542351523 ecr 749350298], length 0 E..4.:@.@................e.s............... .#..,.-. 07:40:31.900128 IP n03.36842 > 192.168.1.148.http-alt: Flags [.], ack 6079, win 501, options [nop,nop,TS val 749350300 ecr 3542351523], length 0 E..4.`@.@....................e.t........... ,.-..#.. 07:40:31.901227 IP n03.http > 192.168.1.228.61961: Flags [P.], seq 1:1636, ack 455, win 501, length 1635: HTTP: HTTP/1.1 302 Found E.....@.@. ..........P. ......~xP....E..HTTP/1.1 302 Found Date: Mon, 27 Feb 2023 07:40:31 GMT Server: Apache/2.4.52 (Ubuntu) Set-Cookie: mod_auth_openidc_state_XgJxHIoQ4MpNsKFXR9f1ukrMojA=vT7CokglE0lF2LTn.9R_U-5e69XmmOQqn0JaTPKnt-ww57V0NUrbliYaB--omiKAGHg9IP-khWdoAr8k_MYnxajhsOmoP1QE1jycK8yKEv1S1h4zk27VqiDeW2oIGFvIEpHv7k6cLLOQET244AchlX9exJbONOqWof4wDSBcTrT2QAKwMUFz5qgIktwqxVWGJtjmZApWGxOR9EUh1y59z7ys_B7FfnpLBrzsAsflDiCVX8cVH0VuZN7e1ZrVqfG9QelL9z6cQGhDkA_BTB3LGrSyPR-UxRh-8KnPrGe_0kwJ2nnlr4AvJgbrDerSAxjA4E8QImQAc9fQz71m7KON93A5hDZJaPbKEtDzkY0IRAQ9nTmmLxvlrVPz0kBGGAh2SphyL6DPCp5SQShM7BWZgVgHqDhxZnzrgAliA7_VrLLllpCq-vJm9.KioAtKGrwun4DYHsZhpvbw; Path=/; HttpOnly Cache-Control: no-cache, no-store, max-age=0 Location: http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth?response_type=code&scope=openid&client_id=apache24&state=XgJxHIoQ4MpNsKFXR9f1ukrMojA&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback&nonce=t0OxJmpOwUpKCAxOfIwBpdOMCq8YX_zf0cKMoYDaj2Q Content-Length: 552 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>302 Found</title> </head><body> <h1>Found</h1> <p>The document has moved <a href="http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth?response_type=code&scope=openid&client_id=apache24&state=XgJxHIoQ4MpNsKFXR9f1ukrMojA&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback&nonce=t0OxJmpOwUpKCAxOfIwBpdOMCq8YX_zf0cKMoYDaj2Q">here</a>.</p> <hr> <address>Apache/2.4.52 (Ubuntu) Server at 192.168.1.147 Port 80</address> </body></html> 07:40:31.901873 IP 192.168.1.228.61961 > n03.http: Flags [.], ack 1636, win 513, length 0 E..(-.@...HU......... .P..~x...3P............. 07:40:36.907511 IP n03.http > 192.168.1.228.61961: Flags [F.], seq 1636, ack 455, win 501, length 0 E..(..@.@............P. ...3..~xP....... 07:40:36.907945 IP 192.168.1.228.61961 > n03.http: Flags [.], ack 1637, win 513, length 0 E..(-.@...HI......... .P..~x...4P............. [ログイン]CF 07:40:56.721473 IP 192.168.1.228.61961 > n03.http: Flags [F.], seq 455, ack 1637, win 513, length 0 E..(-.@...H5......... .P..~x...4P............. 07:40:56.721511 IP n03.http > 192.168.1.228.61961: Flags [.], ack 456, win 501, length 0 E..(..@.@............P. ...4..~yP....... 07:40:56.868722 IP 192.168.1.228.61962 > n03.http: Flags [P.], seq 1:1202, ack 1, win 513, length 1201: HTTP: GET /private/callback?state=XgJxHIoQ4MpNsKFXR9f1ukrMojA&session_state=382e9f57-7812-482b-81df-0bea66d7f9a1&code=e75630b6-50fe-4ca9-a3fc-92106dc09f51.382e9f57-7812-482b-81df-0bea66d7f9a1.2dd726c9-e815-42e6-8c53-b57bd27bb3b0 HTTP/1.1 E...-.@...C.......... .PS.......P...<...GET /private/callback?state=XgJxHIoQ4MpNsKFXR9f1ukrMojA&session_state=382e9f57-7812-482b-81df-0bea66d7f9a1&code=e75630b6-50fe-4ca9-a3fc-92106dc09f51.382e9f57-7812-482b-81df-0bea66d7f9a1.2dd726c9-e815-42e6-8c53-b57bd27bb3b0 HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 Cookie: mod_auth_openidc_state_XgJxHIoQ4MpNsKFXR9f1ukrMojA=vT7CokglE0lF2LTn.9R_U-5e69XmmOQqn0JaTPKnt-ww57V0NUrbliYaB--omiKAGHg9IP-khWdoAr8k_MYnxajhsOmoP1QE1jycK8yKEv1S1h4zk27VqiDeW2oIGFvIEpHv7k6cLLOQET244AchlX9exJbONOqWof4wDSBcTrT2QAKwMUFz5qgIktwqxVWGJtjmZApWGxOR9EUh1y59z7ys_B7FfnpLBrzsAsflDiCVX8cVH0VuZN7e1ZrVqfG9QelL9z6cQGhDkA_BTB3LGrSyPR-UxRh-8KnPrGe_0kwJ2nnlr4AvJgbrDerSAxjA4E8QImQAc9fQz71m7KON93A5hDZJaPbKEtDzkY0IRAQ9nTmmLxvlrVPz0kBGGAh2SphyL6DPCp5SQShM7BWZgVgHqDhxZnzrgAliA7_VrLLllpCq-vJm9.KioAtKGrwun4DYHsZhpvbw 07:40:56.868801 IP n03.http > 192.168.1.228.61962: Flags [.], ack 1202, win 501, length 0 E..(..@.@..Q.........P. ....S...P....... 07:40:56.870293 IP n03.48282 > 192.168.1.148.http-alt: Flags [S], seq 2076852484, win 64240, options [mss 1460,sackOK,TS val 749375270 ecr 0,nop,wscale 7], length 0 E..<+.@.@...............{.A.................... ,..&........ 07:40:56.871229 IP 192.168.1.148.http-alt > n03.48282: Flags [S.], seq 1966052677, ack 2076852485, win 65160, options [mss 1460,sackOK,TS val 3542376494 ecr 749375270,nop,wscale 7], length 0 E..<..@.@..D............u/.E{.A.....2\......... .$`.,..&.... 07:40:56.871301 IP n03.48282 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749375271 ecr 3542376494], length 0 E..4+.@.@...............{.A.u/.F........... ,..'.$`. 07:40:56.871510 IP n03.48282 > 192.168.1.148.http-alt: Flags [P.], seq 1:496, ack 1, win 502, options [nop,nop,TS val 749375272 ecr 3542376494], length 495: HTTP: POST /auth/realms/apache/protocol/openid-connect/token HTTP/1.1 E..#+.@.@...............{.A.u/.F........... ,..(.$`.POST /auth/realms/apache/protocol/openid-connect/token HTTP/1.1 Host: 192.168.1.148:8080 Authorization: Basic YXBhY2hlMjQ6ZmRjYmRlZTctMGYwYS00NzM0LTg5MGItMDI0MmM4MDNjZDNk User-Agent: mod_auth_openidc Accept: */* Content-Type: application/x-www-form-urlencoded Content-Length: 206 grant_type=authorization_code&code=e75630b6-50fe-4ca9-a3fc-92106dc09f51.382e9f57-7812-482b-81df-0bea66d7f9a1.2dd726c9-e815-42e6-8c53-b57bd27bb3b0&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback 07:40:56.871939 IP 192.168.1.148.http-alt > n03.48282: Flags [.], ack 496, win 506, options [nop,nop,TS val 3542376495 ecr 749375272], length 0 E..4.b@.@.).............u/.F{.B.....[...... .$`/,..( 07:40:56.898030 IP 192.168.1.148.http-alt > n03.48282: Flags [P.], seq 1:4136, ack 496, win 506, options [nop,nop,TS val 3542376521 ecr 749375272], length 4135: HTTP: HTTP/1.1 200 OK E..[.c@.@...............u/.F{.B............ .$`I,..(HTTP/1.1 200 OK Cache-Control: no-store X-XSS-Protection: 1; mode=block Pragma: no-cache X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:40:56 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 3769 {"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICItdXFOeTkxeFQ1NHNzbHpqVlNIanhtb2MxaUJ2dklLQVBzMU9zT21zWnZVIn0.eyJleHAiOjE2Nzc0ODM5NTYsImlhdCI6MTY3NzQ4MzY1NiwiYXV0aF90aW1lIjoxNjc3NDgzNjU2LCJqdGkiOiI1MTU3MWVjMC1jYmQ3LTRjYTgtOTZiZS03NDVjMzYwOTc4ZDgiLCJpc3MiOiJodHRwOi8vMTkyLjE2OC4xLjE0ODo4MDgwL2F1dGgvcmVhbG1zL2FwYWNoZSIsImF1ZCI6ImFjY291bnQiLCJzdWIiOiI2NjFjYjViOS03ZGRjLTQyZWUtOGMzMi0xMDE5ZThjYjhmYzgiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJhcGFjaGUyNCIsIm5vbmNlIjoidDBPeEptcE93VXBLQ0F4T2ZJd0JwZE9NQ3E4WVhfemYwY0tNb1lEYWoyUSIsInNlc3Npb25fc3RhdGUiOiIzODJlOWY1Ny03ODEyLTQ4MmItODFkZi0wYmVhNjZkN2Y5YTEiLCJhY3IiOiIxIiwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbImRlZmF1bHQtcm9sZXMtYXBhY2hlIiwib2ZmbGluZV9hY2Nlc3MiLCJ1bWFfYXV0aG9yaXphdGlvbiJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoib3BlbmlkIGVtYWlsIHByb2ZpbGUiLCJzaWQiOiIzODJlOWY1Ny03ODEyLTQ4MmItODFkZi0wYmVhNjZkN2Y5YTEiLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsIm5hbWUiOiJ1c2VyMDFfZmlyc3QgdXNlcjAxX2xhc3QiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJ1c2VyMDEiLCJnaXZlbl9uYW1lIjoidXNlcjAxX2ZpcnN0IiwiZmFtaWx5X25hbWUiOiJ1c2VyMDFfbGFzdCIsImVtYWlsIjoidXNlcjAxQGRlY29kZS5yZWQifQ.HlEgy6GxAE1RIAedF-wLZUlVfzPG7Ui3zBK529QKA_T-doUZTbvsmwgAUXbXFA9Hc2kCS4x6uIZ1TXyMXQ7arZo-F6t8fMkXhQZ82CpslNOOC5IewITnM30ZkXCet6tqG6cd_pCZ78x6myAHkl5BN_RQ-FGWkBbx3W3HFubsrx94-6fMu1GF3sN8vAuYQjlPg2-gilE1mGbPya8Lq0fmx0UB0g_wnNgBA-V9Gxn2h958_993-5DVszbkEwlYnwn8ti8GcGC6w7A8d6LF1BevuYvOmyvnTmEdyJIyhFM5K96Aj-yEyQW31yOk8KVLd5gBjbW7ucJlxIi6RDWv-SO0TA","expires_in":300,"refresh_expires_in":1800,"refresh_token":"eyJhbGciOiJIUzI1 07:40:56.898131 IP n03.48282 > 192.168.1.148.http-alt: Flags [.], ack 4136, win 489, options [nop,nop,TS val 749375298 ecr 3542376521], length 0 E..4+.@.@...............{.B.u/.m........... ,..B.$`I 07:40:56.898388 IP n03.48282 > 192.168.1.148.http-alt: Flags [F.], seq 496, ack 4136, win 501, options [nop,nop,TS val 749375298 ecr 3542376521], length 0 E..4+.@.@...............{.B.u/.m........... ,..B.$`I 07:40:56.898849 IP n03.48284 > 192.168.1.148.http-alt: Flags [S], seq 479458571, win 64240, options [mss 1460,sackOK,TS val 749375299 ecr 0,nop,wscale 7], length 0 E..<.d@.@...................................... ,..C........ 07:40:56.899604 IP 192.168.1.148.http-alt > n03.48284: Flags [S.], seq 2678427846, ack 479458572, win 65160, options [mss 1460,sackOK,TS val 3542376522 ecr 749375299,nop,wscale 7], length 0 E..<..@.@..D.........................Y......... .$`J,..C.... 07:40:56.899681 IP n03.48284 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749375300 ecr 3542376522], length 0 E..4.e@.@.................................. ,..D.$`J 07:40:56.899772 IP n03.48284 > 192.168.1.148.http-alt: Flags [P.], seq 1:136, ack 1, win 502, options [nop,nop,TS val 749375300 ecr 3542376522], length 135: HTTP: GET /auth/realms/apache/protocol/openid-connect/certs HTTP/1.1 E....f@.@.._.........................%..... ,..D.$`JGET /auth/realms/apache/protocol/openid-connect/certs HTTP/1.1 Host: 192.168.1.148:8080 User-Agent: mod_auth_openidc Accept: */* 07:40:56.900375 IP 192.168.1.148.http-alt > n03.48284: Flags [.], ack 136, win 509, options [nop,nop,TS val 3542376523 ecr 749375300], length 0 E..4..@.@..P.........................(..... .$`K,..D 07:40:56.903710 IP 192.168.1.148.http-alt > n03.48282: Flags [F.], seq 4136, ack 497, win 506, options [nop,nop,TS val 3542376526 ecr 749375298], length 0 E..4.f@.@.).............u/.m{.B.....Kc..... .$`N,..B 07:40:56.903758 IP n03.48282 > 192.168.1.148.http-alt: Flags [.], ack 4137, win 501, options [nop,nop,TS val 749375304 ecr 3542376526], length 0 E..4+.@.@...............{.B.u/.n........... ,..H.$`N 07:40:56.931852 IP 192.168.1.148.http-alt > n03.48284: Flags [P.], seq 1:3263, ack 136, win 509, options [nop,nop,TS val 3542376554 ecr 749375300], length 3262: HTTP: HTTP/1.1 200 OK E.....@.@............................\..... .$`j,..DHTTP/1.1 200 OK Cache-Control: no-cache X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:40:56 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 2914 {"keys":[{"kid":"-uqNy91xT54sslzjVSHjxmoc1iBvvIKAPs1OsOmsZvU","kty":"RSA","alg":"RS256","use":"sig","n":"lgTq04NxaAwy6eB3Pna7zGwy0IQLzPy2ehILfhXX057JK8KERMt04ABovJbuVR_S45nRjZluOeYtJHXo1TAmS_YTemLJFFHt4H5dwxUeeJPcDGAQA_qjOAFeZBKVcd_-ElL1X0NFUXtUwpdoKUjQAHxgnha8DPIOE1-w4GJE2kBNgEnS4MnpP0ymTLrKx9s4BfSm4eD7zee0odDaYNsX2RwQimhEgU9gTOK5Q4H6qwmFc2vQlcpLjVxTm5kCO-ph5VXIHpR5tzxaVGI3N_Yo5q9-7ng3cbTsJUG-o0dZ2o-lTcp2J8lguVk51nDxQ_JWxf3orujuPJy2jvtHj3mBkQ","e":"AQAB","x5c":["MIICmzCCAYMCBgGGgmfZYTANBgkqhkiG9w0BAQsFADARMQ8wDQYDVQQDDAZhcGFjaGUwHhcNMjMwMjI0MDc0OTQ5WhcNMzMwMjI0MDc1MTI5WjARMQ8wDQYDVQQDDAZhcGFjaGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCWBOrTg3FoDDLp4Hc+drvMbDLQhAvM/LZ6Egt+FdfTnskrwoREy3TgAGi8lu5VH9LjmdGNmW455i0kdejVMCZL9hN6YskUUe3gfl3DFR54k9wMYBAD+qM4AV5kEpVx3/4SUvVfQ0VRe1TCl2gpSNAAfGCeFrwM8g4TX7DgYkTaQE2ASdLgyek/TKZMusrH2zgF9Kbh4PvN57Sh0Npg2xfZHBCKaESBT2BM4rlDgfqrCYVza9CVykuNXFObmQI76mHlVcgelHm3PFpUYjc39ijmr37ueDdxtOwlQb6jR1naj6VNynYnyWC5WTnWcPFD8lbF/eiu6O48nLaO+0ePeYGRAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAC93c/GNjNITAiFqt6eMADfW6wGTI5tngQbDmSKV0YyWmB9AENEko0ZcvvISHYB2BMBkvIcYmOu5cdw8euTmzcZvGmEsRd6W5EpEueBLpWb8RoBBZb+EFclJ0kcRDvRAOdIe2dLh+Kg28TLyKPcfAhE7bFkvx/2N+dKxRWSaQyMu7PqaLRixQPvjPz8whEuDwLqTjZtlX3h1NBgx+38h453mfE/wV1YOQkT8VejhFdOalwxAX6xxnJ2o8Ifx7n39YObKqOi5NbnOM22D9DS3LANqfaokRx9gBWpTM4w0XpsunUUzryFLMreF9ftyz0lF2MDkzYsqLfwrsVlHRxeBLu0="],"x5t":"oO4sY7Yy_0AYR3MkAHvV1DLwK4U","x5t#S256":"MY99HCZ3vUzqaz9m8WF7s7JJh1SV35qtRVlpFeapH8c"},{"kid":"SJj7ggz1KV0aWrxDzej2cXV5XHHvXAqa9OLSgf8RchA","kty":"RSA","alg":"RS256","use":"enc","n":"kLXRA9_4uqa1o5QFBSOMsJqyUoxvohZtfYNaQ6Hf9OjmSam54e9umOdIlp3VJ0682aWHbocW7zsiO 07:40:56.931917 IP n03.48284 > 192.168.1.148.http-alt: Flags [.], ack 3263, win 489, options [nop,nop,TS val 749375332 ecr 3542376554], length 0 E..4.g@.@.................................. ,..d.$`j 07:40:56.932172 IP n03.48284 > 192.168.1.148.http-alt: Flags [F.], seq 136, ack 3263, win 501, options [nop,nop,TS val 749375332 ecr 3542376554], length 0 E..4.h@.@.................................. ,..d.$`j 07:40:56.932746 IP n03.48298 > 192.168.1.148.http-alt: Flags [S], seq 927095172, win 64240, options [mss 1460,sackOK,TS val 749375333 ecr 0,nop,wscale 7], length 0 E..<..@.@..C............7BY.................... ,..e........ 07:40:56.933461 IP 192.168.1.148.http-alt > n03.48298: Flags [S.], seq 1743728180, ack 927095173, win 65160, options [mss 1460,sackOK,TS val 3542376556 ecr 749375333,nop,wscale 7], length 0 E..<..@.@..D............g..47BY......(......... .$`l,..e.... 07:40:56.933461 IP 192.168.1.148.http-alt > n03.48284: Flags [F.], seq 3263, ack 137, win 509, options [nop,nop,TS val 3542376556 ecr 749375332], length 0 E..4..@.@..L.........................'..... .$`l,..d 07:40:56.933517 IP n03.48298 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749375334 ecr 3542376556], length 0 E..4..@.@..J............7BY.g..5........... ,..f.$`l 07:40:56.933556 IP n03.48284 > 192.168.1.148.http-alt: Flags [.], ack 3264, win 501, options [nop,nop,TS val 749375334 ecr 3542376556], length 0 E..4.i@.@.................................. ,..f.$`l 07:40:56.933597 IP n03.48298 > 192.168.1.148.http-alt: Flags [P.], seq 1:1684, ack 1, win 502, options [nop,nop,TS val 749375334 ecr 3542376556], length 1683: HTTP: GET /auth/realms/apache/protocol/openid-connect/userinfo HTTP/1.1 E.....@.@...............7BY.g..5.....1..... ,..f.$`lGET /auth/realms/apache/protocol/openid-connect/userinfo HTTP/1.1 Host: 192.168.1.148:8080 User-Agent: mod_auth_openidc Accept: */* Authorization: Bearer eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICItdXFOeTkxeFQ1NHNzbHpqVlNIanhtb2MxaUJ2dklLQVBzMU9zT21zWnZVIn0.eyJleHAiOjE2Nzc0ODM5NTYsImlhdCI6MTY3NzQ4MzY1NiwiYXV0aF90aW1lIjoxNjc3NDgzNjU2LCJqdGkiOiI1MTU3MWVjMC1jYmQ3LTRjYTgtOTZiZS03NDVjMzYwOTc4ZDgiLCJpc3MiOiJodHRwOi8vMTkyLjE2OC4xLjE0ODo4MDgwL2F1dGgvcmVhbG1zL2FwYWNoZSIsImF1ZCI6ImFjY291bnQiLCJzdWIiOiI2NjFjYjViOS03ZGRjLTQyZWUtOGMzMi0xMDE5ZThjYjhmYzgiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJhcGFjaGUyNCIsIm5vbmNlIjoidDBPeEptcE93VXBLQ0F4T2ZJd0JwZE9NQ3E4WVhfemYwY0tNb1lEYWoyUSIsInNlc3Npb25fc3RhdGUiOiIzODJlOWY1Ny03ODEyLTQ4MmItODFkZi0wYmVhNjZkN2Y5YTEiLCJhY3IiOiIxIiwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbImRlZmF1bHQtcm9sZXMtYXBhY2hlIiwib2ZmbGluZV9hY2Nlc3MiLCJ1bWFfYXV0aG9yaXphdGlvbiJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoib3BlbmlkIGVtYWlsIHByb2ZpbGUiLCJzaWQiOiIzODJlOWY1Ny03ODEyLTQ4MmItODFkZi0wYmVhNjZkN2Y5YTEiLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsIm5hbWUiOiJ1c2VyMDFfZmlyc3QgdXNlcjAxX2xhc3QiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJ1c2VyMDEiLCJnaXZlbl9uYW1lIjoidXNlcjAxX2ZpcnN0IiwiZmFtaWx5X25hbWUiOiJ1c2VyMDFfbGFzdCIsImVtYWlsIjoidXNlcjAxQGRlY29kZS5yZWQifQ.HlEgy6GxAE1RIAedF-wLZUlVfzPG7Ui3zBK529QKA_T-doUZTbvsmwgAUXbXFA9Hc2kCS4x6uIZ1TXyMXQ7arZo-F6t8fMkXhQZ82CpslNOOC5IewITnM30ZkXCet6tqG6cd_pCZ78x6myAHkl5BN_RQ-FGWkBbx3W3HFubsrx94-6fMu1GF3sN8vAuYQjlPg2-gilE1mGbPya8Lq0fmx0UB0g_wnNgBA-V9Gxn2h958_993-5DVszbkEwlYnwn8ti8GcGC6w7A8d6LF1BevuYvOmyvnTmEdyJIyhFM5K96Aj-yEyQW31yOk8KVLd5gBjbW7ucJlxIi6RDWv-SO0TA 07:40:56.934152 IP 192.168.1.148.http-alt > n03.48298: Flags [.], ack 1684, win 496, options [nop,nop,TS val 3542376557 ecr 749375334], length 0 E..4]_@.@.X.............g..57B`............ .$`m,..f 07:40:56.952768 IP 192.168.1.148.http-alt > n03.48298: Flags [P.], seq 1:565, ack 1684, win 501, options [nop,nop,TS val 3542376575 ecr 749375334], length 564: HTTP: HTTP/1.1 200 OK E..h]`@.@.V.............g..57B`............ .$`.,..fHTTP/1.1 200 OK Cache-Control: no-cache X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:40:56 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 217 {"sub":"661cb5b9-7ddc-42ee-8c32-1019e8cb8fc8","email_verified":false,"name":"user01_first user01_last","preferred_username":"user01","given_name":"user01_first","family_name":"user01_last","email":"user01@decode.red"} 07:40:56.952851 IP n03.48298 > 192.168.1.148.http-alt: Flags [.], ack 565, win 501, options [nop,nop,TS val 749375353 ecr 3542376575], length 0 E..4..@.@..G............7B`.g.0i........... ,..y.$`. 07:40:56.953080 IP n03.48298 > 192.168.1.148.http-alt: Flags [F.], seq 1684, ack 565, win 501, options [nop,nop,TS val 749375353 ecr 3542376575], length 0 E..4..@.@..F............7B`.g.0i........... ,..y.$`. 07:40:56.953646 IP n03.http > 192.168.1.228.61962: Flags [P.], seq 1:780, ack 1202, win 501, length 779: HTTP: HTTP/1.1 302 Found E..3..@.@..D.........P. ....S...P.......HTTP/1.1 302 Found Date: Mon, 27 Feb 2023 07:40:56 GMT Server: Apache/2.4.52 (Ubuntu) Set-Cookie: mod_auth_openidc_state_XgJxHIoQ4MpNsKFXR9f1ukrMojA=; Path=/; Expires=Thu, 01 Jan 1970 00:00:00 GMT; HttpOnly Set-Cookie: mod_auth_openidc_session=fed7b24d-5b97-4688-925a-a256b702cece; Path=/; HttpOnly Location: http://192.168.1.147/private/page.html Content-Length: 301 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>302 Found</title> </head><body> <h1>Found</h1> <p>The document has moved <a href="http://192.168.1.147/private/page.html">here</a>.</p> <hr> <address>Apache/2.4.52 (Ubuntu) Server at 192.168.1.147 Port 80</address> </body></html> 07:40:56.957751 IP 192.168.1.228.61962 > n03.http: Flags [P.], seq 1202:1753, ack 780, win 510, length 551: HTTP: GET /private/page.html HTTP/1.1 E..O-.@...F ......... .PS.......P....D..GET /private/page.html HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 Cookie: mod_auth_openidc_session=fed7b24d-5b97-4688-925a-a256b702cece 07:40:56.957846 IP n03.http > 192.168.1.228.61962: Flags [.], ack 1753, win 501, length 0 E..(..@.@..O.........P. ....S...P....... 07:40:56.958489 IP n03.http > 192.168.1.228.61962: Flags [P.], seq 780:1084, ack 1753, win 501, length 304: HTTP: HTTP/1.1 200 OK E..X..@.@............P. ....S...P.......HTTP/1.1 200 OK Date: Mon, 27 Feb 2023 07:40:56 GMT Server: Apache/2.4.52 (Ubuntu) Last-Modified: Fri, 24 Feb 2023 08:08:10 GMT ETag: "16-5f56da14f0b99" Accept-Ranges: bytes Content-Length: 22 Keep-Alive: timeout=5, max=99 Connection: Keep-Alive Content-Type: text/html <h3>Private Page</h3> |
Implicit Flow
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 |
n@n03:~$ sudo tcpdump -A -s 2048 -i enp0s3 \(\(src host 192.168.1.147\) and \(dst host 192.168.1.228\)\) or \(\(src host 192.168.1.228\) and \(dst host 192.168.1.147\)\) or \(\(src host 192.168.1.147\) and \(dst host 192.168.1.148\)\) or \(\(src host 192.168.1.148\) and \(dst host 192.168.1.147\)\) and not port 22 and tcp tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on enp0s3, link-type EN10MB (Ethernet), snapshot length 2048 bytes 07:44:31.819049 IP 192.168.1.228.62128 > n03.http: Flags [S], seq 4062353291, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 E..4.\@...G............P."..........r............... 07:44:31.819049 IP 192.168.1.228.62129 > n03.http: Flags [S], seq 2760552383, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 E..4.]@...G............P............................ 07:44:31.819177 IP n03.http > 192.168.1.228.62128: Flags [S.], seq 2187049476, ack 4062353292, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 E..4..@.@............P...[..."...................... 07:44:31.819576 IP n03.http > 192.168.1.228.62129: Flags [S.], seq 1768014674, ack 2760552384, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 E..4..@.@............P..ia.R........................ 07:44:31.819971 IP 192.168.1.228.62128 > n03.http: Flags [.], ack 1, win 513, length 0 E..(.^@...G............P."...[..P...o......... 07:44:31.819971 IP 192.168.1.228.62128 > n03.http: Flags [P.], seq 1:481, ack 1, win 513, length 480: HTTP: GET /private/page.html HTTP/1.1 E...._@...E............P."...[..P.......GET /private/page.html HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 07:44:31.819971 IP 192.168.1.228.62129 > n03.http: Flags [.], ack 1, win 513, length 0 E..(.`@...G............P....ia.SP.... ........ 07:44:31.819999 IP n03.http > 192.168.1.228.62128: Flags [.], ack 481, win 501, length 0 E..(..@.@............P...[...".lP....... 07:44:31.821534 IP n03.35478 > 192.168.1.148.http-alt: Flags [S], seq 1201059574, win 64240, options [mss 1460,sackOK,TS val 749590222 ecr 0,nop,wscale 7], length 0 E..<..@.@..y............G...................... ,........... 07:44:31.822287 IP 192.168.1.148.http-alt > n03.35478: Flags [S.], seq 2614954671, ack 1201059575, win 65160, options [mss 1460,sackOK,TS val 3542591445 ecr 749590222,nop,wscale 7], length 0 E..<..@.@..D.............. .G........4......... .'..,....... 07:44:31.822371 IP n03.35478 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749590222 ecr 3542591445], length 0 E..4..@.@...............G..... ............ ,....'.. 07:44:31.822475 IP n03.35478 > 192.168.1.148.http-alt: Flags [P.], seq 1:139, ack 1, win 502, options [nop,nop,TS val 749590223 ecr 3542591445], length 138: HTTP: GET /auth/realms/apache/.well-known/openid-configuration HTTP/1.1 E.....@.@...............G..... ......(..... ,....'..GET /auth/realms/apache/.well-known/openid-configuration HTTP/1.1 Host: 192.168.1.148:8080 User-Agent: mod_auth_openidc Accept: */* 07:44:31.822959 IP 192.168.1.148.http-alt > n03.35478: Flags [.], ack 139, win 508, options [nop,nop,TS val 3542591446 ecr 749590223], length 0 E..4..@.@.0A.............. .G......."...... .'..,... 07:44:31.827595 IP 192.168.1.148.http-alt > n03.35478: Flags [P.], seq 1:6078, ack 139, win 508, options [nop,nop,TS val 3542591450 ecr 749590223], length 6077: HTTP: HTTP/1.1 200 OK E.....@.@................. .G........[..... .'..,...HTTP/1.1 200 OK Cache-Control: no-cache, must-revalidate, no-transform, no-store X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:44:31 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 5688 {"issuer":"http://192.168.1.148:8080/auth/realms/apache","authorization_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth","token_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/token","introspection_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/token/introspect","userinfo_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/userinfo","end_session_endpoint":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/logout","jwks_uri":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/certs","check_session_iframe":"http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/login-status-iframe.html","grant_types_supported":["authorization_code","implicit","refresh_token","password","client_credentials","urn:ietf:params:oauth:grant-type:device_code","urn:openid:params:grant-type:ciba"],"response_types_supported":["code","none","id_token","token","id_token token","code id_token","code token","code id_token token"],"subject_types_supported":["public","pairwise"],"id_token_signing_alg_values_supported":["PS384","ES384","RS384","HS256","HS512","ES256","RS256","HS384","ES512","PS256","PS512","RS512"],"id_token_encryption_alg_values_supported":["RSA-OAEP","RSA-OAEP-256","RSA1_5"],"id_token_encryption_enc_values_supported":["A256GCM","A192GCM","A128GCM","A128CBC-HS256","A192CBC-HS384","A256CBC-HS512"],"userinfo_signing_alg_values_supported":["PS384","ES384","RS384","HS256","HS512","ES256","RS256","HS384","ES512" 07:44:31.827704 IP n03.35478 > 192.168.1.148.http-alt: Flags [.], ack 6078, win 474, options [nop,nop,TS val 749590228 ecr 3542591450], length 0 E..4..@.@..~............G....."m........... ,....'.. 07:44:31.827855 IP n03.35478 > 192.168.1.148.http-alt: Flags [F.], seq 139, ack 6078, win 501, options [nop,nop,TS val 749590228 ecr 3542591450], length 0 E..4..@.@..}............G....."m........... ,....'.. 07:44:31.828968 IP 192.168.1.148.http-alt > n03.35478: Flags [F.], seq 6078, ack 140, win 508, options [nop,nop,TS val 3542591451 ecr 749590228], length 0 E..4..@.@.0;.............."mG....... 9..... .'..,... 07:44:31.828990 IP n03.35478 > 192.168.1.148.http-alt: Flags [.], ack 6079, win 501, options [nop,nop,TS val 749590229 ecr 3542591451], length 0 E..4..@.@..|............G....."n........... ,....'.. 07:44:31.829864 IP n03.http > 192.168.1.228.62128: Flags [P.], seq 1:1679, ack 481, win 501, length 1678: HTTP: HTTP/1.1 302 Found E.....@.@............P...[...".lP....p..HTTP/1.1 302 Found Date: Mon, 27 Feb 2023 07:44:31 GMT Server: Apache/2.4.52 (Ubuntu) Set-Cookie: mod_auth_openidc_state_yqF8aiXNIZn246UMhOJofXYL8k4=5tUQcdtJTDDAvdM_.eoSncQwyHLVSQJXa4HXthFdRW9jsdumOAiUhYP4Q-DQdxVvu75bEIT5pwPMMkjh7dum48EzydXa0ImcnFF_oCnvDie4FpxlL59XSMQot9f8Aczu40oMY8iXKVVd1Nm5OHak55X62PabzTCTVdq1VjZ_XaQvp450aVky0SjiYmc86owFkZ2xjxH2UeD6-v-sQOIsNEynN8lHm6vp1GGF_IRNAw2JiJPbUinmCNxTliAxTUxUSbwvkPQQ4yTxxR29XbN8RAsWT6urywVf7_n7smzygkZyuDrhMHVE1MQeVISyDYuOOC3Jdot1ENGfE3eKBTNf4wQe0rSOd0Tfw3HfubpWzQTZa30XpmXDY5GLQ82B0tCeRVyP4FByKFS_VV7R2lnLl9OyslNyBvQLu_a9ozY7YEgDMOYWd25TmQiAWBpLACXeNNM5zlhQ.gWbsNRXYdCdtPtuXHpeDgA; Path=/; HttpOnly Cache-Control: no-cache, no-store, max-age=0 Location: http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth?response_type=token%20id_token&scope=openid&client_id=apache24&state=yqF8aiXNIZn246UMhOJofXYL8k4&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback&nonce=-HLdM8yvyIPVYgcbuCM8Oi9C8lYO0CwtZJHkD07KLVM Content-Length: 564 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>302 Found</title> </head><body> <h1>Found</h1> <p>The document has moved <a href="http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth?response_type=token%20id_token&scope=openid&client_id=apache24&state=yqF8aiXNIZn246UMhOJofXYL8k4&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback&nonce=-HLdM8yvyIPVYgcbuCM8Oi9C8lYO0CwtZJHkD07KLVM">here</a>.</p> <hr> <address>Apache/2.4.52 (Ubuntu) Server at 192.168.1.147 Port 80</address> </body></html> 07:44:31.830253 IP 192.168.1.228.62128 > n03.http: Flags [.], ack 1679, win 513, length 0 E..(.a@...G............P.".l.[..P...g......... [ログイン]IF 07:44:36.834447 IP n03.http > 192.168.1.228.62128: Flags [F.], seq 1679, ack 481, win 501, length 0 E..(..@.@............P...[...".lP....... 07:44:36.834704 IP 192.168.1.228.62128 > n03.http: Flags [.], ack 1680, win 513, length 0 E..(.s@...G............P.".l.[..P...g......... 07:44:40.737718 IP 192.168.1.228.62128 > n03.http: Flags [F.], seq 481, ack 1680, win 513, length 0 E..(.u@...G............P.".l.[..P...g......... 07:44:40.737752 IP n03.http > 192.168.1.228.62128: Flags [.], ack 482, win 501, length 0 E..(..@.@............P...[...".mP...g... 07:44:40.841530 IP 192.168.1.228.62129 > n03.http: Flags [P.], seq 1:1020, ack 1, win 513, length 1019: HTTP: GET /private/callback HTTP/1.1 E..#.w@...C............P....ia.SP.......GET /private/callback HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 Cookie: mod_auth_openidc_state_yqF8aiXNIZn246UMhOJofXYL8k4=5tUQcdtJTDDAvdM_.eoSncQwyHLVSQJXa4HXthFdRW9jsdumOAiUhYP4Q-DQdxVvu75bEIT5pwPMMkjh7dum48EzydXa0ImcnFF_oCnvDie4FpxlL59XSMQot9f8Aczu40oMY8iXKVVd1Nm5OHak55X62PabzTCTVdq1VjZ_XaQvp450aVky0SjiYmc86owFkZ2xjxH2UeD6-v-sQOIsNEynN8lHm6vp1GGF_IRNAw2JiJPbUinmCNxTliAxTUxUSbwvkPQQ4yTxxR29XbN8RAsWT6urywVf7_n7smzygkZyuDrhMHVE1MQeVISyDYuOOC3Jdot1ENGfE3eKBTNf4wQe0rSOd0Tfw3HfubpWzQTZa30XpmXDY5GLQ82B0tCeRVyP4FByKFS_VV7R2lnLl9OyslNyBvQLu_a9ozY7YEgDMOYWd25TmQiAWBpLACXeNNM5zlhQ.gWbsNRXYdCdtPtuXHpeDgA 07:44:40.841567 IP n03.http > 192.168.1.228.62129: Flags [.], ack 1020, win 501, length 0 E..(.&@.@............P..ia.S....P....... 07:44:40.841996 IP n03.http > 192.168.1.228.62129: Flags [P.], seq 1:1333, ack 1020, win 501, length 1332: HTTP: HTTP/1.1 200 OK E..\.'@.@............P..ia.S....P.......HTTP/1.1 200 OK Date: Mon, 27 Feb 2023 07:44:40 GMT Server: Apache/2.4.52 (Ubuntu) Content-Length: 1141 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd"> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <title>Submitting...</title> <script type="text/javascript"> function postOnLoad() { encoded = location.hash.substring(1).split('&'); for (i = 0; i < encoded.length; i++) { encoded[i].replace(/\+/g, ' '); var n = encoded[i].indexOf('='); var input = document.createElement('input'); input.type = 'hidden'; input.name = decodeURIComponent(encoded[i].substring(0, n)); input.value = decodeURIComponent(encoded[i].substring(n+1)); document.forms[0].appendChild(input); } document.forms[0].action = window.location.href.substr(0, window.location.href.indexOf('#')); document.forms[0].submit(); } </script> </head> <body onload="postOnLoad()"> <p>Submitting...</p> <form method="post" action=""> <p> <input type="hidden" name="response_mode" value="fragment"> </p> </form> </body> </html> 07:44:40.886805 IP 192.168.1.228.62129 > n03.http: Flags [.], ack 1333, win 508, length 0 E..(.y@...G............P....ia..P............. 07:44:41.233993 IP 192.168.1.228.62139 > n03.http: Flags [S], seq 1614646462, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 E..4.{@...G............P`=...........P.............. 07:44:41.234109 IP n03.http > 192.168.1.228.62139: Flags [S.], seq 4062347940, ack 1614646463, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 E..4..@.@............P..."..`=...................... 07:44:41.234573 IP 192.168.1.228.62139 > n03.http: Flags [.], ack 1, win 4100, length 0 E..(.|@...G............P`=..."..P....7........ 07:44:41.235143 IP 192.168.1.228.62129 > n03.http: Flags [P.], seq 1020:2189, ack 1333, win 508, length 1169: HTTP: POST /private/callback HTTP/1.1 E....}@...B............P....ia..P...g...POST /private/callback HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Content-Length: 3007 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://192.168.1.147 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Referer: http://192.168.1.147/private/callback Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 Cookie: mod_auth_openidc_state_yqF8aiXNIZn246UMhOJofXYL8k4=5tUQcdtJTDDAvdM_.eoSncQwyHLVSQJXa4HXthFdRW9jsdumOAiUhYP4Q-DQdxVvu75bEIT5pwPMMkjh7dum48EzydXa0ImcnFF_oCnvDie4FpxlL59XSMQot9f8Aczu40oMY8iXKVVd1Nm5OHak55X62PabzTCTVdq1VjZ_XaQvp450aVky0SjiYmc86owFkZ2xjxH2UeD6-v-sQOIsNEynN8lHm6vp1GGF_IRNAw2JiJPbUinmCNxTliAxTUxUSbwvkPQQ4yTxxR29XbN8RAsWT6urywVf7_n7smzygkZyuDrhMHVE1MQeVISyDYuOOC3Jdot1ENGfE3eKBTNf4wQe0rSOd0Tfw3HfubpWzQTZa30XpmXDY5GLQ82B0tCeRVyP4FByKFS_VV7R2lnLl9OyslNyBvQLu_a9ozY7YEgDMOYWd25TmQiAWBpLACXeNNM5zlhQ.gWbsNRXYdCdtPtuXHpeDgA 07:44:41.235143 IP 192.168.1.228.62129 > n03.http: Flags [P.], seq 2189:5196, ack 1333, win 508, length 3007: HTTP E....~@...;............P...Lia..P.......response_mode=fragment&state=yqF8aiXNIZn246UMhOJofXYL8k4&session_state=de5b4422-d9fc-4dd1-aeff-95834ef0c595&id_token=eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICItdXFOeTkxeFQ1NHNzbHpqVlNIanhtb2MxaUJ2dklLQVBzMU9zT21zWnZVIn0.eyJleHAiOjE2Nzc0ODQ3ODAsImlhdCI6MTY3NzQ4Mzg4MCwiYXV0aF90aW1lIjoxNjc3NDgzODgwLCJqdGkiOiJkNDA1MmQ2YS1lYTJjLTRkZDUtOWYzYi0xNmU3OTZjZmIzNDUiLCJpc3MiOiJodHRwOi8vMTkyLjE2OC4xLjE0ODo4MDgwL2F1dGgvcmVhbG1zL2FwYWNoZSIsImF1ZCI6ImFwYWNoZTI0Iiwic3ViIjoiNjYxY2I1YjktN2RkYy00MmVlLThjMzItMTAxOWU4Y2I4ZmM4IiwidHlwIjoiSUQiLCJhenAiOiJhcGFjaGUyNCIsIm5vbmNlIjoiLUhMZE04eXZ5SVBWWWdjYnVDTThPaTlDOGxZTzBDd3RaSkhrRDA3S0xWTSIsInNlc3Npb25fc3RhdGUiOiJkZTViNDQyMi1kOWZjLTRkZDEtYWVmZi05NTgzNGVmMGM1OTUiLCJhdF9oYXNoIjoiVnc4Mll5TFNKdU5jenZQTUo1dnRHQSIsImFjciI6IjEiLCJzX2hhc2giOiJhYU1HWHM0QzRTbWFzTldCQXhjOHN3Iiwic2lkIjoiZGU1YjQ0MjItZDlmYy00ZGQxLWFlZmYtOTU4MzRlZjBjNTk1IiwiZW1haWxfdmVyaWZpZWQiOmZhbHNlLCJuYW1lIjoidXNlcjAxX2ZpcnN0IHVzZXIwMV9sYXN0IiwicHJlZmVycmVkX3VzZXJuYW1lIjoidXNlcjAxIiwiZ2l2ZW5fbmFtZSI6InVzZXIwMV9maXJzdCIsImZhbWlseV9uYW1lIjoidXNlcjAxX2xhc3QiLCJlbWFpbCI6InVzZXIwMUBkZWNvZGUucmVkIn0.Kv_u3YTCk6y0RX6ZUNRM-_bEqaE1q4ry8aM5NAW80Ycu1YgtPgrhCCuglUebPKBgY6M_9th0vmrdizdiQYVTJo3M-hSNxgHuVn32z6miUNcuXCws6jIz9YVcjczcepSfVHqFLnX9mAeFIRVXSad1L9losGOZspaH-olS4CMM6bIovSE4nFfw-PTlcCF4mTimDyygEqgjaMuUDh7VPm4bIVYw01ed9MlNhvJRzU-3HkOHSiUx9I1vXQ3qjNrpwlcOUZkDP3cN5MMLfL8lsY0GLWDzoPRT9G0UEof-iMErUWRtPi4a5uJpiMzkdS13o2Br5pUR6Ww9ZGNV8qkb7yi0rg&access_token=eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICItdXFOeTkxeFQ1NHNzbHpqVlNIanhtb2MxaUJ2dklLQVBzMU9zT21zWnZVIn0.eyJleHAiOjE2Nzc0ODQ3ODAsImlhdCI6MTY3NzQ4Mzg4MCwiYXV0aF90aW1lIjoxNjc3NDgzODgwLCJqdGkiOiJlYjA0MzU1ZC1hZGI0LTQxOGQtOTA4MC1iYWFkYzgwNDI3YTgiLCJpc3MiOiJodHRwOi8vMTkyLjE2OC4xLjE0ODo4MDgwL2F1dGgvcmVhbG1zL2FwYWNoZSIsImF1ZCI6ImFjY291bnQiLCJzdWIiOiI2NjFjYjViOS03ZGRjLTQyZWUtOGMzMi0xMDE5ZThjYjhmYzgiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJhcGFjaGUyNCIsIm5vbmNlIjoiLUhMZE04eXZ5SVBWWWdjYnVDTThPaTlDOGxZTzBDd3RaSkhrRDA3S0xWTSIsInNlc3Npb25fc3RhdGUiOiJkZ 07:44:41.235471 IP n03.http > 192.168.1.228.62129: Flags [.], ack 5196, win 501, length 0 E..(.(@.@............P..ia......P....... 07:44:41.236464 IP n03.35490 > 192.168.1.148.http-alt: Flags [S], seq 4019417032, win 64240, options [mss 1460,sackOK,TS val 749599637 ecr 0,nop,wscale 7], length 0 E..<=.@.@.xz..............o.................... ,........... 07:44:41.237473 IP 192.168.1.148.http-alt > n03.35490: Flags [S.], seq 524794994, ack 4019417033, win 65160, options [mss 1460,sackOK,TS val 3542600860 ecr 749599637,nop,wscale 7], length 0 E..<..@.@..D.............G.r..o................ .'..,....... 07:44:41.237554 IP n03.35490 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749599638 ecr 3542600860], length 0 E..4=.@.@.x...............o..G.s........... ,....'.. 07:44:41.237740 IP n03.35490 > 192.168.1.148.http-alt: Flags [P.], seq 1:136, ack 1, win 502, options [nop,nop,TS val 749599638 ecr 3542600860], length 135: HTTP: GET /auth/realms/apache/protocol/openid-connect/certs HTTP/1.1 E...=.@.@.w...............o..G.s.....%..... ,....'..GET /auth/realms/apache/protocol/openid-connect/certs HTTP/1.1 Host: 192.168.1.148:8080 User-Agent: mod_auth_openidc Accept: */* 07:44:41.238767 IP 192.168.1.148.http-alt > n03.35490: Flags [.], ack 136, win 509, options [nop,nop,TS val 3542600861 ecr 749599638], length 0 E..4M.@.@.h..............G.s..pP....Bm..... .'..,... 07:44:41.247391 IP 192.168.1.148.http-alt > n03.35490: Flags [P.], seq 1:3263, ack 136, win 509, options [nop,nop,TS val 3542600870 ecr 749599638], length 3262: HTTP: HTTP/1.1 200 OK E...M.@.@.[..............G.s..pP.....\..... .'..,...HTTP/1.1 200 OK Cache-Control: no-cache X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:44:41 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 2914 {"keys":[{"kid":"-uqNy91xT54sslzjVSHjxmoc1iBvvIKAPs1OsOmsZvU","kty":"RSA","alg":"RS256","use":"sig","n":"lgTq04NxaAwy6eB3Pna7zGwy0IQLzPy2ehILfhXX057JK8KERMt04ABovJbuVR_S45nRjZluOeYtJHXo1TAmS_YTemLJFFHt4H5dwxUeeJPcDGAQA_qjOAFeZBKVcd_-ElL1X0NFUXtUwpdoKUjQAHxgnha8DPIOE1-w4GJE2kBNgEnS4MnpP0ymTLrKx9s4BfSm4eD7zee0odDaYNsX2RwQimhEgU9gTOK5Q4H6qwmFc2vQlcpLjVxTm5kCO-ph5VXIHpR5tzxaVGI3N_Yo5q9-7ng3cbTsJUG-o0dZ2o-lTcp2J8lguVk51nDxQ_JWxf3orujuPJy2jvtHj3mBkQ","e":"AQAB","x5c":["MIICmzCCAYMCBgGGgmfZYTANBgkqhkiG9w0BAQsFADARMQ8wDQYDVQQDDAZhcGFjaGUwHhcNMjMwMjI0MDc0OTQ5WhcNMzMwMjI0MDc1MTI5WjARMQ8wDQYDVQQDDAZhcGFjaGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCWBOrTg3FoDDLp4Hc+drvMbDLQhAvM/LZ6Egt+FdfTnskrwoREy3TgAGi8lu5VH9LjmdGNmW455i0kdejVMCZL9hN6YskUUe3gfl3DFR54k9wMYBAD+qM4AV5kEpVx3/4SUvVfQ0VRe1TCl2gpSNAAfGCeFrwM8g4TX7DgYkTaQE2ASdLgyek/TKZMusrH2zgF9Kbh4PvN57Sh0Npg2xfZHBCKaESBT2BM4rlDgfqrCYVza9CVykuNXFObmQI76mHlVcgelHm3PFpUYjc39ijmr37ueDdxtOwlQb6jR1naj6VNynYnyWC5WTnWcPFD8lbF/eiu6O48nLaO+0ePeYGRAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAC93c/GNjNITAiFqt6eMADfW6wGTI5tngQbDmSKV0YyWmB9AENEko0ZcvvISHYB2BMBkvIcYmOu5cdw8euTmzcZvGmEsRd6W5EpEueBLpWb8RoBBZb+EFclJ0kcRDvRAOdIe2dLh+Kg28TLyKPcfAhE7bFkvx/2N+dKxRWSaQyMu7PqaLRixQPvjPz8whEuDwLqTjZtlX3h1NBgx+38h453mfE/wV1YOQkT8VejhFdOalwxAX6xxnJ2o8Ifx7n39YObKqOi5NbnOM22D9DS3LANqfaokRx9gBWpTM4w0XpsunUUzryFLMreF9ftyz0lF2MDkzYsqLfwrsVlHRxeBLu0="],"x5t":"oO4sY7Yy_0AYR3MkAHvV1DLwK4U","x5t#S256":"MY99HCZ3vUzqaz9m8WF7s7JJh1SV35qtRVlpFeapH8c"},{"kid":"SJj7ggz1KV0aWrxDzej2cXV5XHHvXAqa9OLSgf8RchA","kty":"RSA","alg":"RS256","use":"enc","n":"kLXRA9_4uqa1o5QFBSOMsJqyUoxvohZtfYNaQ6Hf9OjmSam54e9umOdIlp3VJ0682aWHbocW7zsiO 07:44:41.247492 IP n03.35490 > 192.168.1.148.http-alt: Flags [.], ack 3263, win 489, options [nop,nop,TS val 749599648 ecr 3542600870], length 0 E..4=.@.@.x...............pP.G.1........... ,....'.. 07:44:41.247652 IP n03.35490 > 192.168.1.148.http-alt: Flags [F.], seq 136, ack 3263, win 501, options [nop,nop,TS val 749599648 ecr 3542600870], length 0 E..4=.@.@.x~..............pP.G.1........... ,....'.. 07:44:41.248517 IP n03.35500 > 192.168.1.148.http-alt: Flags [S], seq 4292020369, win 64240, options [mss 1460,sackOK,TS val 749599649 ecr 0,nop,wscale 7], length 0 E..<`.@.@.V.................................... ,........... 07:44:41.250062 IP 192.168.1.148.http-alt > n03.35500: Flags [S.], seq 3143152284, ack 4292020370, win 65160, options [mss 1460,sackOK,TS val 3542600873 ecr 749599649,nop,wscale 7], length 0 E..<..@.@..D.............X...........6......... .'..,....... 07:44:41.250192 IP n03.35500 > 192.168.1.148.http-alt: Flags [.], ack 1, win 502, options [nop,nop,TS val 749599650 ecr 3542600873], length 0 E..4`/@.@.V..................X............. ,....'.. 07:44:41.250374 IP n03.35500 > 192.168.1.148.http-alt: Flags [P.], seq 1:1684, ack 1, win 502, options [nop,nop,TS val 749599650 ecr 3542600873], length 1683: HTTP: GET /auth/realms/apache/protocol/openid-connect/userinfo HTTP/1.1 E...`0@.@.O..................X.......1..... ,....'..GET /auth/realms/apache/protocol/openid-connect/userinfo HTTP/1.1 Host: 192.168.1.148:8080 User-Agent: mod_auth_openidc Accept: */* Authorization: Bearer eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICItdXFOeTkxeFQ1NHNzbHpqVlNIanhtb2MxaUJ2dklLQVBzMU9zT21zWnZVIn0.eyJleHAiOjE2Nzc0ODQ3ODAsImlhdCI6MTY3NzQ4Mzg4MCwiYXV0aF90aW1lIjoxNjc3NDgzODgwLCJqdGkiOiJlYjA0MzU1ZC1hZGI0LTQxOGQtOTA4MC1iYWFkYzgwNDI3YTgiLCJpc3MiOiJodHRwOi8vMTkyLjE2OC4xLjE0ODo4MDgwL2F1dGgvcmVhbG1zL2FwYWNoZSIsImF1ZCI6ImFjY291bnQiLCJzdWIiOiI2NjFjYjViOS03ZGRjLTQyZWUtOGMzMi0xMDE5ZThjYjhmYzgiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJhcGFjaGUyNCIsIm5vbmNlIjoiLUhMZE04eXZ5SVBWWWdjYnVDTThPaTlDOGxZTzBDd3RaSkhrRDA3S0xWTSIsInNlc3Npb25fc3RhdGUiOiJkZTViNDQyMi1kOWZjLTRkZDEtYWVmZi05NTgzNGVmMGM1OTUiLCJhY3IiOiIxIiwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbImRlZmF1bHQtcm9sZXMtYXBhY2hlIiwib2ZmbGluZV9hY2Nlc3MiLCJ1bWFfYXV0aG9yaXphdGlvbiJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoib3BlbmlkIGVtYWlsIHByb2ZpbGUiLCJzaWQiOiJkZTViNDQyMi1kOWZjLTRkZDEtYWVmZi05NTgzNGVmMGM1OTUiLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsIm5hbWUiOiJ1c2VyMDFfZmlyc3QgdXNlcjAxX2xhc3QiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJ1c2VyMDEiLCJnaXZlbl9uYW1lIjoidXNlcjAxX2ZpcnN0IiwiZmFtaWx5X25hbWUiOiJ1c2VyMDFfbGFzdCIsImVtYWlsIjoidXNlcjAxQGRlY29kZS5yZWQifQ.PEHtvc2_J7sqMI62VCZ8O9W0m9_qlwqv79R6DtxxbgckaZOo4osfWpaLRvXDnvhkGhGNUFbozCHhyrFO1ckx70toDEZaSasnonCYZ37EuD3GqfpgnqTqemUlE3J0vhTAoiyukB7k4F4eNaaXkd8QGx71_EQ1ecIgDdQ9GFaYY8p4HYSR3JKtmL9VlJEe7_b2gXxOJEAWGvWN1QxzJCHH_xr9r3sJtrQ5q4ZemiBJ32pjPUAiPfBqgbOmKVZom_HyqXrtXLt39QbisF_p0uh8SsZv5vB5zvbkYs7FKZsYjnwzpq7dSMn20s0oou0X8FveVChKRTiEoBCKRHGZFHyzcg 07:44:41.250556 IP 192.168.1.148.http-alt > n03.35490: Flags [F.], seq 3263, ack 137, win 509, options [nop,nop,TS val 3542600873 ecr 749599648], length 0 E..4M.@.@.h..............G.1..pQ....5...... .'..,... 07:44:41.250569 IP n03.35490 > 192.168.1.148.http-alt: Flags [.], ack 3264, win 501, options [nop,nop,TS val 749599651 ecr 3542600873], length 0 E..4=.@.@.x}..............pQ.G.2........... ,....'.. 07:44:41.251489 IP 192.168.1.148.http-alt > n03.35500: Flags [.], ack 1684, win 496, options [nop,nop,TS val 3542600874 ecr 749599650], length 0 E..4..@.@.'..............X.....%........... .'..,... 07:44:41.271970 IP 192.168.1.148.http-alt > n03.35500: Flags [P.], seq 1:565, ack 1684, win 501, options [nop,nop,TS val 3542600894 ecr 749599650], length 564: HTTP: HTTP/1.1 200 OK E..h..@.@.%S.............X.....%........... .'..,...HTTP/1.1 200 OK Cache-Control: no-cache X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN Referrer-Policy: no-referrer Date: Mon, 27 Feb 2023 07:44:41 GMT Connection: keep-alive Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: application/json Content-Length: 217 {"sub":"661cb5b9-7ddc-42ee-8c32-1019e8cb8fc8","email_verified":false,"name":"user01_first user01_last","preferred_username":"user01","given_name":"user01_first","family_name":"user01_last","email":"user01@decode.red"} 07:44:41.272072 IP n03.35500 > 192.168.1.148.http-alt: Flags [.], ack 565, win 501, options [nop,nop,TS val 749599672 ecr 3542600894], length 0 E..4`2@.@.V................%.X............. ,....'.. 07:44:41.272373 IP n03.35500 > 192.168.1.148.http-alt: Flags [F.], seq 1684, ack 565, win 501, options [nop,nop,TS val 749599672 ecr 3542600894], length 0 E..4`3@.@.V................%.X............. ,....'.. 07:44:41.272899 IP n03.http > 192.168.1.228.62129: Flags [P.], seq 1333:2111, ack 5196, win 501, length 778: HTTP: HTTP/1.1 302 Found E..2.)@.@............P..ia......P.......HTTP/1.1 302 Found Date: Mon, 27 Feb 2023 07:44:41 GMT Server: Apache/2.4.52 (Ubuntu) Set-Cookie: mod_auth_openidc_state_yqF8aiXNIZn246UMhOJofXYL8k4=; Path=/; Expires=Thu, 01 Jan 1970 00:00:00 GMT; HttpOnly Set-Cookie: mod_auth_openidc_session=3b4eccbb-8960-4849-bc96-4efdd451fe31; Path=/; HttpOnly Location: http://192.168.1.147/private/page.html Content-Length: 301 Keep-Alive: timeout=5, max=99 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>302 Found</title> </head><body> <h1>Found</h1> <p>The document has moved <a href="http://192.168.1.147/private/page.html">here</a>.</p> <hr> <address>Apache/2.4.52 (Ubuntu) Server at 192.168.1.147 Port 80</address> </body></html> 07:44:41.273739 IP 192.168.1.148.http-alt > n03.35500: Flags [F.], seq 565, ack 1685, win 501, options [nop,nop,TS val 3542600896 ecr 749599672], length 0 E..4..@.@.'..............X.....&........... .'..,... 07:44:41.273752 IP n03.35500 > 192.168.1.148.http-alt: Flags [.], ack 566, win 501, options [nop,nop,TS val 749599674 ecr 3542600896], length 0 E..4`4@.@.V................&.X............. ,....'.. 07:44:41.276585 IP 192.168.1.228.62129 > n03.http: Flags [P.], seq 5196:5795, ack 2111, win 513, length 599: HTTP: GET /private/page.html HTTP/1.1 E.....@...E0...........P....ia..P....\..GET /private/page.html HTTP/1.1 Host: 192.168.1.147 Connection: keep-alive Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Referer: http://192.168.1.147/private/callback Accept-Encoding: gzip, deflate Accept-Language: ja,en-US;q=0.9,en;q=0.8 Cookie: mod_auth_openidc_session=3b4eccbb-8960-4849-bc96-4efdd451fe31 07:44:41.277825 IP n03.http > 192.168.1.228.62129: Flags [P.], seq 2111:2415, ack 5795, win 501, length 304: HTTP: HTTP/1.1 200 OK E..X.*@.@............P..ia.....bP.......HTTP/1.1 200 OK Date: Mon, 27 Feb 2023 07:44:41 GMT Server: Apache/2.4.52 (Ubuntu) Last-Modified: Fri, 24 Feb 2023 08:08:10 GMT ETag: "16-5f56da14f0b99" Accept-Ranges: bytes Content-Length: 22 Keep-Alive: timeout=5, max=98 Connection: Keep-Alive Content-Type: text/html <h3>Private Page</h3> |
※クライアント・クレデンシャルズフロー
参考) https://www.appsdeveloperblog.com/keycloak-client-credentials-grant-example/
管理画面より
クライアントの設定
・Service Accounts Enabled : ON
クライアントのCredentials
・シークレットキーのコピー
access_tokenの取得
curl –location –request POST ‘http://localhost:8080/auth/realms/demo/protocol/openid-connect/token’ \
–header ‘Content-Type: application/x-www-form-urlencoded’ \
–data-urlencode ‘client_id=client-credentials’ \
–data-urlencode ‘client_secret=9e9aad32-e86f-4b48-a657-4e89004c0706’ \
–data-urlencode ‘scope=email’ \
–data-urlencode ‘grant_type=client_credentials’ | jq
上記アクセストークンを使用して、イントロスペクションの実行(トークンが有効なら、”active”: true)
参考) https://docs.nginx.com/nginx-management-suite/acm/tutorials/introspection-keycloak
curl -D – –location –request POST ‘http://localhost:8080/auth/realms/demo/protocol/openid-connect/token/introspect’ \
–header ‘Content-Type: application/x-www-form-urlencoded’ \
–data-urlencode ‘client_id=client-credentials’ \
–data-urlencode ‘client_secret=9e9aad32-e86f-4b48-a657-4e89004c0706’ \
–data-urlencode ‘token=eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSl…………’
/etc/apache2/mods-enabled/auth_openidc.conf に追記
OIDCPKCEMethod S256
※認可コードフロー(Code Flow)の設定がベース
設定をすると、リクエストパラメータに
code_challenge
code_challenge_method
code_verifier
が追加される
n03->ブラウザ(Location)
http://192.168.1.148:8080/auth/realms/apache/protocol/openid-connect/auth?response_type=code&scope=openid&client_id=apache24&state=bSMPa_w34-G0o7TMXIU3n5ikvq8&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback&nonce=Y6-q5o3HlwTcQv6P7aDfl6rV0rVFwb2XnzGvauv-XPo&code_challenge=IAMPa5v90qbL6S-00U05Mp4AYz9le9CAfEVyafQNVOg&code_challenge_method=S256
n03->n07
POST /auth/realms/apache/protocol/openid-connect/token
grant_type=authorization_code&code=0451bf18-9b23-4e8f-bfb9-db80ba587bef.0d2983c3-13e5-4dd5-b9e0-c4a1aa702044.2dd726c9-e815-42e6-8c53-b57bd27bb3b0&redirect_uri=http%3A%2F%2F192.168.1.147%2Fprivate%2Fcallback&code_verifier=hTezQCGJsHONEMFEN3PussSXcpnAujk2VzH8McJi2BY